Image Credit to japanese.engadget.com
Tech News
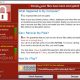
The original WannaCry 2.0 is a failure to try the work! True 3.0 variant version has begun to be infected, but fortunately ..
Comaeio founder Matthieu Suiche found the latest variant of WannaCry from the newly infected computer, this new variant has not been found in Kaspersky Lab yesterday, “Kill Switch version”, but has switched to the new Kill Switch address.
The original attack has been stalled
The original version of the use of iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com as Kill Switch self-destruction switch, then MalwareTech’s heart to find and the first time to register the name, temporarily stop the new theory of proliferation.
Kill Switch is not an attacker conscience
Here it is first to deconstruct why the virus will set the Kill Switch self-destruction switch, of course, not for the final conscience, but to escape the anti-virus software analysis. Antivirus software is intended to be a virus file, set up a virtual operating environment, this environment will block any of the virus network connection, but at the same time will create a false response to the virus that a successful connection, cited it to attack.
Wannacry’s self-destruction switch is used to detect whether it is in an antivirus software under the virtual environment, the above domain name should be no one registered, so will not get any DNS response, but if the anti-virus virtual environment, Response, so if Wannacry know the environment under the anti-virus software, will stop the action to avoid being detected to kill, and wait for other opportunities on the computer.
2.0 is not finished ransomware
So yesterday, Kaspersky Lab global research and analysis group director Costin Raiu confirmed to foreign media, no Kill Switch’s “perfect version” WannaCry has come. But Matthieu Suiche found that this version of the damage can only be part of the operation, I believe that the attacker’s unfinished failure works, although not lethal but there is still communication, and therefore does not constitute a security threat.
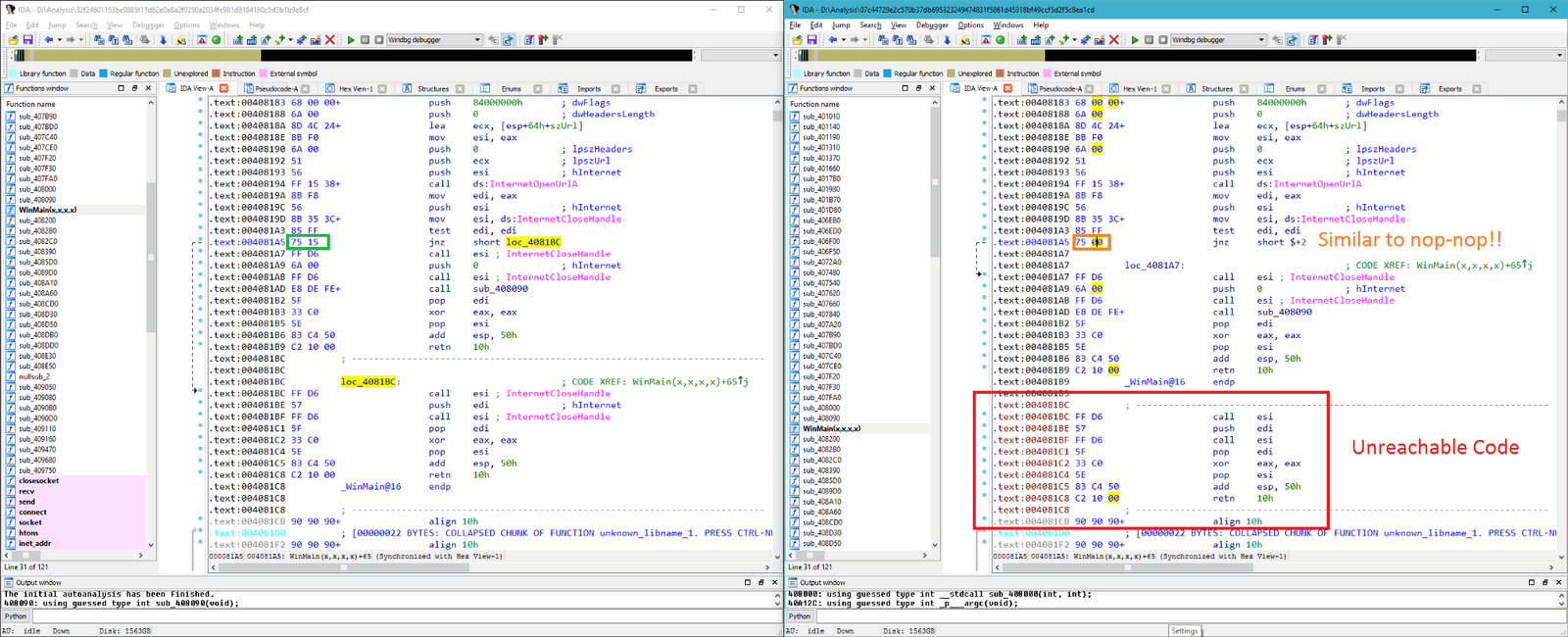
image credit to unwire.hk
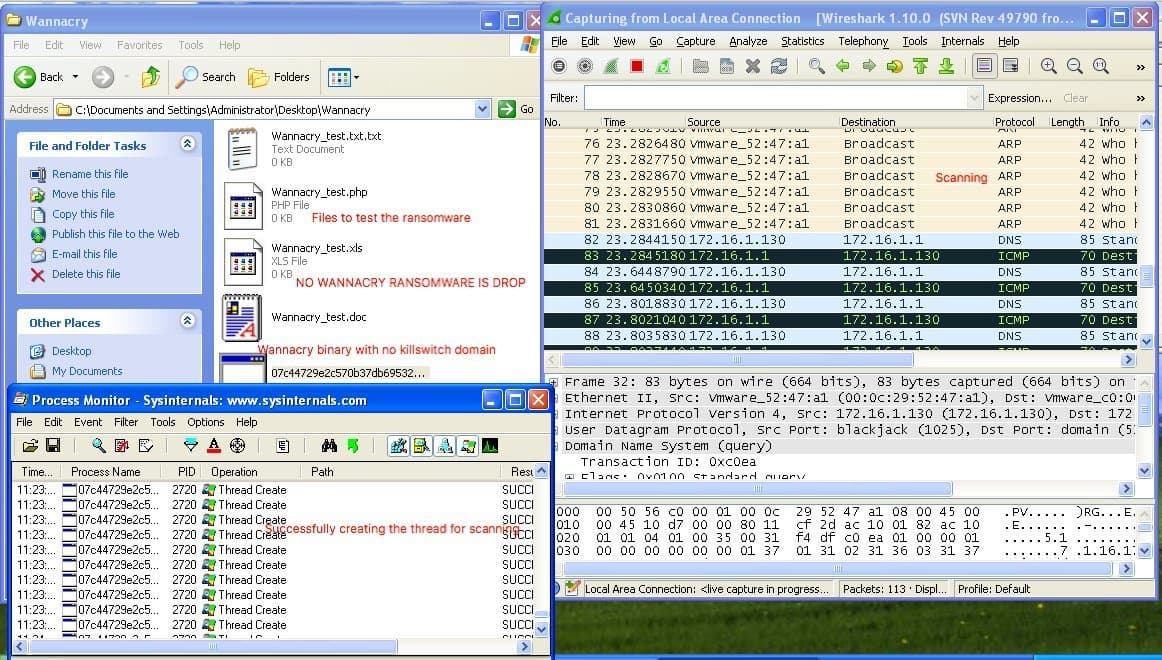
image credit to unwire.hk
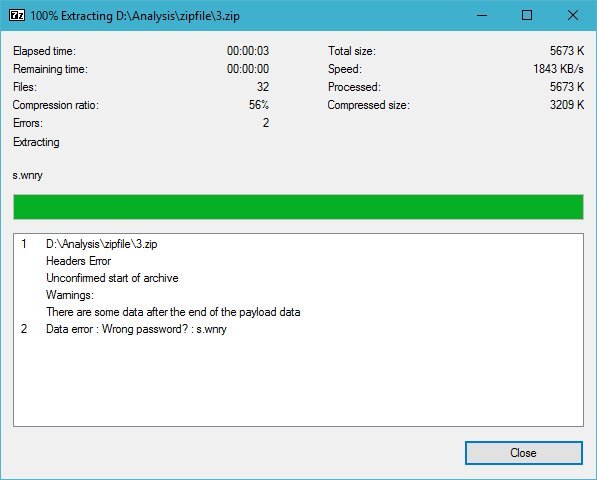
image credit to unwire.hk
2.0 virus packets damaged, some files can not be extracted
Real 3.0 version of the blaze
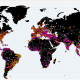
But the story is not over, 3.0 new variants from the newly infected computer was detected by Matthieu Suiche reverse crack and found using ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com as the new Kill Switch address, fortunately Matt immediately with the same way to buy the first Domain name, to prevent the spread. And the number of links is synchronized to the real-time Wanna Cry infection map
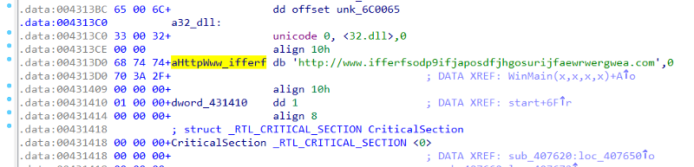
image credit to unwire.hk
Conclusion:
Update your operating system as fast as possible.
Can get the patch file here
Share this to your friends that we interested.


Leave a Reply
Want to join the discussion?Feel free to contribute!