Step 1:Configure openvpn for the bandwidth control.
In this case we will use below number for the private ip.
Ikev2=24 #eth0 tcp1194=23 #tun3 tcp443=22 #tun4 udp1194=21 #tun0 udp4096=25 #tun1 udp80=20 #tun2 pptp=111 l2tp=30 main=eth0
In openvpn case because of openvpn have the tun+ tunnel interface for each port.
we have to do it in other ways, just a slightly different compare with ikev2
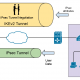
in this case we going to demonstrate the udp1194 openvpn default port.
add below command to define the tun0 interface.
tc qdisc add dev tun0 root handle 1: htb
and how do i control that udp1194 is under tun0, we can just configure on /etc/openvpn/server.conf
dev tun
and we specific the tun interface number like this
dev tun0
so that after the openvpn restart we can actually confirm that udp1194 port is listening on tun0 interface, and to make sure we are accurate controlling the right interface.
Step2: Set the marking with iptables based on the unique private ip address
udp1194=21
iptables -I FORWARD -s 10.$udp1194.$udp1194.1 -j MARK --set-mark 11 iptables -I FORWARD -d 10.$udp1194.$udp1194.1 -j MARK --set-mark 11
Step3: Define all the rules and setup the filtering.
Define the classid for interface eth0 and tun0, why we still need to setup the rules for eth0?
because of tun0 only can control the user upload speed, we still need control the download speed for the user, so we have to use eth0.
eth0
tc class add dev eth0 parent 1:1 classid 1:11 htb rate 1mbit ceil 1mbit tc qdisc add dev eth0 parent 1:11 sfq perturb 10 tc filter add dev eth0 protocol ip parent 1: prio 1 handle 11 fw flowid 1:11
tun0
tc class add dev tun0 parent 1:1 classid 1:11 htb rate 1mbit ceil 1mbit tc qdisc add dev tun0 parent 1:11 sfq perturb 10 tc filter add dev tun0 protocol ip parent 1: prio 1 handle 11 fw flowid 1:11
That the only thing we have to do.
if u want to filter all the user on the server based on openvpn.
we have a scripts below to let you actually setup a set of rules to filtering the user speed.
#/bin/bash
udp1194=21 #tun0
echo tc qdisc del dev $main root >>tcrules
echo tc qdisc del dev tun0 root >>tcrules
echo tc qdisc add dev $main root handle 1: htb >>tcrules
echo tc qdisc add dev tun0 root handle 1: htb >>tcrules
for i in {1..254}
do
##udp1194
echo iptables -I FORWARD -s 10.$udp1194.$id.$i -j MARK --set-mark 1$i >> mark
echo iptables -I FORWARD -d 10.$udp1194.$id.$i -j MARK --set-mark 1$i >> mark
echo tc class add dev eth0 parent 1:1 classid 1:1$i htb rate 1mbit ceil 1mbit >> tcrules
echo tc qdisc add dev eth0 parent 1:1$i sfq perturb 10 >> tcrules
echo tc filter add dev eth0 protocol ip parent 1: prio 1 handle 1$i fw flowid 1:1$i >> tcrules
echo tc class add dev tun0 parent 1:1 classid 1:1$i htb rate 1mbit ceil 1mbit >> tcrules
echo tc qdisc add dev tun0 parent 1:1$i sfq perturb 10 >> tcrules
echo tc filter add dev tun0 protocol ip parent 1: prio 1 handle 1$i fw flowid 1:1$i >> tcrules
done
put all this in the scripts, and chmod 755 to make the scripts executable , and bash scriptsname.
and u will see it will generate 2 scripts in the current location which is mark and tcrules. Just run it and can verify the result for marking by
iptables-save |grep mark
it will show the below result as per your configuration.
-A FORWARD -s 10.21.21.49/32 -j MARK –set-xmark 0x2ed/0xffffffff
-A FORWARD -d 10.21.21.49/32 -j MARK –set-xmark 0x1c1/0xffffffff
and use below command to actually show the class and qdisc that you set earlier for tc.
tc -s -d class show dev eth0 tc -s -d qdisc show dev eth0 tc -s -d class show dev tun0 tc -s -d qdisc show dev tun0
If this article help, just share it to your friends.



Leave a Reply
Want to join the discussion?Feel free to contribute!